CompTIA CySA+ (Cyber Security Analyst+)
Training Schedule and Pricing
Our training model blends knowledge and certification prep into one solution. Interact face-to-face with vendor certified trainers AT OUR TRAINING CENTER IN SARASOTA, FL - OR - attend the same instructor-led live camp ONLINE.
-
May062024Delivery Format:REMOTE CLASSROOM LIVEDate:05.06.2024 - 05.10.2024Location:ONLINEPrice Includes:Instructor Led Class, Official Courseware, Labs and Exams$2,9955 days
-
Jun172024Delivery Format:REMOTE CLASSROOM LIVEDate:06.17.2024 - 06.21.2024Location:ONLINEPrice Includes:Instructor Led Class, Official Courseware, Labs and Exams$2,9955 days
-
Jul152024Delivery Format:REMOTE CLASSROOM LIVEDate:07.15.2024 - 07.19.2024Location:ONLINEPrice Includes:Instructor Led Class, Official Courseware, Labs and Exams$2,9955 days
What's Included
1 CompTIA Test Vouchers
CompTIA Training Books
1 Retake Vouchers (if needed)
CompTIA Study Labs & Simulations
Instructor Led Live Training
Our official CompTIA CySA+ bootcamp uses the official courseware and students take the official exam to achieve the CompTIA CySA+ certification. We offer the most comprehensive classroom training and certification testing. You attend training and test for your certification at the same facility.
Students will gain the skills to troubleshoot via customized hacks and build solid solutions. Students will also gain the skills to demonstrate that you can provide the best cybersecurity solutions and protection for organizations worldwide.
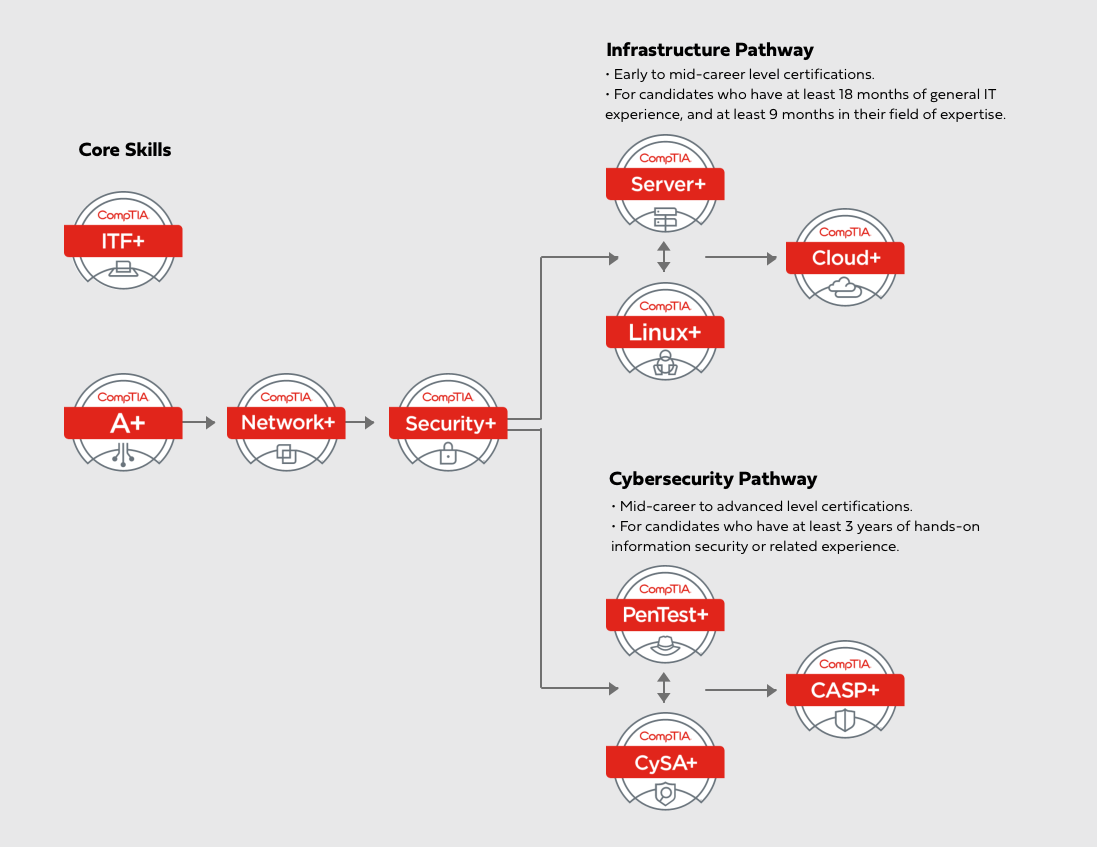
CompTIA Cybersecurity Analyst + meets the ISO 17024 standard and is approved by U.S. Department of Defense to fulfill Directive 8570.01-M requirements. It is compliant with government regulations under the Federal Information Security Management Act (FISMA).
The CySA+ boot camp incorporates CompTIA Official Courses -
CompTIA (CySA+) CS0-003
Topics covered in this boot camp:
Assess information security risk in computing and network environments.
Analyze reconnaissance threats to computing and network environments.
Analyze attacks on computing and network environments.
Analyze post-attack techniques on computing and network environments.
Implement a vulnerability management program.
Collect cybersecurity intelligence.
Analyze data collected from security and event logs.
Perform active analysis on assets and networks.
Respond to cybersecurity incidents.
Investigate cybersecurity incidents.
Address security issues with the organization's technology architecture.
Topics Covered in this Official Boot Camp
Assessing Information Security Risk
- Identify the Importance of Risk Management
- Assess Risk
- Mitigate Risk
- Integrate Documentation into Risk Management
Analyzing Reconnaissance Threats to Computing and Network Environments
- Assess the Impact of Reconnaissance Incidents
- Assess the Impact of Social Engineering
Analyzing Attacks on Computing and Network Environments
- Assess the Impact of System Hacking Attacks
- Assess the Impact of Web-Based Attacks
- Assess the Impact of Malware
- Assess the Impact of Hijacking and Impersonation Attacks
- Assess the Impact of DoS Incidents
- Assess the Impact of Threats to Mobile Security
- Assess the Impact of Threats to Cloud Security
Analyzing Post-Attack Techniques
- Assess Command and Control Techniques
- Assess Persistence Techniques
- Assess Lateral Movement and Pivoting Techniques
- Assess Data Exfiltration Techniques
- Assess Anti-Forensics Techniques
Managing Vulnerabilities in the Organization
- Implement a Vulnerability Management Plan
- Assess Common Vulnerabilities
- Conduct Vulnerability Scans
- Conduct Penetration Tests on Network Assets
Collecting Cybersecurity Intelligence
- Deploy a Security Intelligence Collection and Analysis Platform
- Collect Data from Network-Based Intelligence Sources
- Collect Data from Host-Based Intelligence Sources
Analyzing Log Data
- Use Common Tools to Analyze Logs
- Use SIEM Tools for Analysis
Performing Active Asset and Network Analysis
- Analyze Incidents with Windows-Based Tools
- Analyze Incidents with Linux-Based Tools
- Analyze Malware
- Analyze Indicators of Compromise
Responding to Cybersecurity Incidents
- Deploy an Incident Handling and Response Architecture
- Mitigate Incidents
- Prepare for Forensic Investigation as a CSIRT
Investigating Cybersecurity Incidents
- Apply a Forensic Investigation Plan
- Securely Collect and Analyze Electronic Evidence
- Follow Up on the Results of an Investigation
Addressing Security Architecture Issues
- Remediate Identity and Access Management Issues
- Implement Security During the SDLC
CERTIFICATION CAMPS FACILITIES
CAMPUS - Certification Camps built out a stand alone training center (not a hotel conference room) with spacious classrooms, new desk, Herman Miller Aeron chairs & comfortable common areas. Each student has a dedicated desk with two monitors. Each classroom has a maximum of two rows - so everyone is able to be engaged without the "back row" feeling.
CLASSROOM EQUIPMENT - Students work on a dedicated Dell Client Desktop with 32GB memory with 512GB SSD drives - All Labs are executed the extremely fast Microsoft Data Center Hosted Lab Environment .
CAMPUS INTERNET - The campus is connected with a 1Gbps (1,000 Mbps) Verizon Fios Business Connection which provides complete internet (including VPN) access for students.
COMMON AREA - Amenties including snacks, drinks (Coffee, 100% juices, sodas, etc) all complimentary.
LODGING - We use the Hyatt Place Lakewood Ranch. This "upgraded" hotel offers extremely comfortable beds, great breakfast and very fast internet access.
NEAR BY - Many shops, restaurants and grocery options are available within walking distance. Additionally - the hotel provided scheduled shuttle services. Restaurants like Cheesecake Factory, California Pizza Kitchen, Panera Bread, Bone Fish Grill, Ruby Tuesday's, Five Guys, Chipotle, Chili's and over 20 additional choices in the immediate area.